Concepts
STRA Training Videos
Security Threat and Risk Assessment Training 101
In this training video we take a deep dive into security threat and risk assessments.
Security Threat and Risk Assessment Training - 101 - Slide Deck
Security Threat and Risk Assessment Training - 101 - Slide Deck with speaking notes transcript
Security Threat and Risk Assessment Training - 101 - Slide Deck (PDF)
Understanding the reference STRA process
A SOAR is the final artifact produced for a Security Threat and Risk Assessment. This training video will help you understand, in detail, how to complete a Statement of Acceptable Risks (SOAR).
Understanding and completing the SOAR course
This training video covers the Province of British Columbia’s recommended reference process for conducting Security Threat and Risk Assessments (STRA). Once you have watched this you will better understand the steps required to complete an STRA from beginning to end.
What is a “risk”?
- An acknowledgment of how likely a threat is to leverage a vulnerability, what the potential impacts could be, and what it means to the organization
The goal of “Information Security”
- to reduce information security risk to the organization
- to protect confidentiality, availability, and integrity
- to build trust and confidence from stakeholders (e.g. citizens)
The goal of “risk management”
- to identify potential problems before they occur
- so that risk-handling activities may be planned and invoked
- as needed across the life of the system to mitigate adverse impacts on achieving objectives
The goal of a “risk assessment”
- snap-shot in time of risks
- then identify a treatment plan
- elevate risks to an appropriate person in your organization for review and acceptance of the risks as stated and the treatment plan
- and mitigate, remediate, transfer, or avoid the risk(s)
- log any residual risks to a risk register
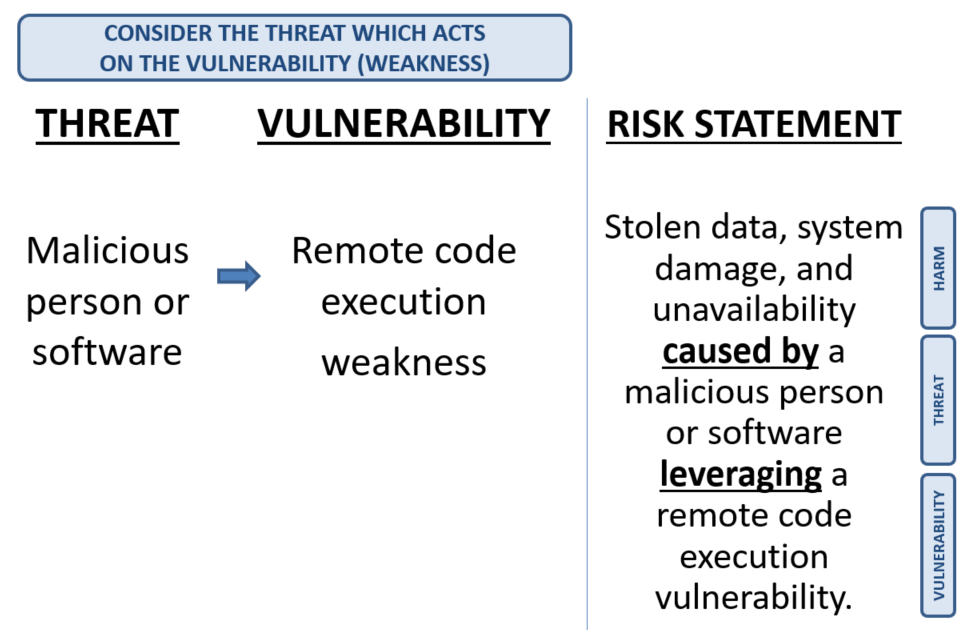
How to define a risk statement
- [HARM] caused by [THREAT] leveraging [VULNERABILITY]
EXAMPLE …
How to rate risks
Formula: Likelihood (L) * Impact (I) = Risk Rating (RR)
Risk rating matrix:
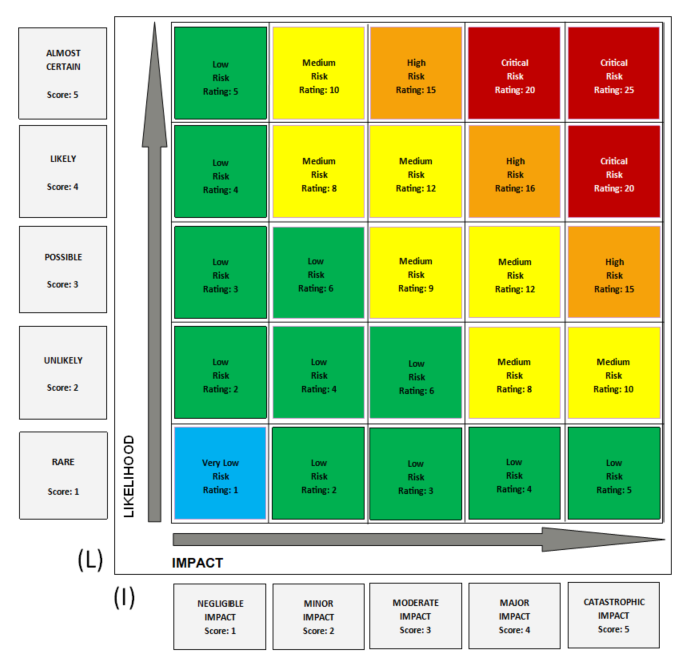
What do the different risk rating levels mean?
“Very Low” Risk —> Rating = 1
Risk exists and is tolerable. It should be controlled, and minimal treatment efforts should be maintained. The risk state may not improve over time. These risks do not receive priority attention.
“Low” Risk —> Rating = 2 to 7
Risk exists and is tolerable. It should be controlled, and treatment efforts should be maintained. The risk state may take a long period of time to improve. These risks do not receive priority attention.
“Medium” Risk —> Rating = 8 to 14
Risk should be reduced but may be tolerated if the treatment cost exceeds the cost of the risk’s potential impact.
“High” Risk —> Rating = 15 to 16
Risk should be reduced but may be tolerated for a short period if the cost is prohibitive or the identified treatment would result in other adverse impacts.
“Critical” Risk —> Rating = 17 to 25
Unacceptable risk which cannot be justified except in very special circumstances. Resources to treat should be made available immediately with little resistance or barriers. Treatment of critical risks should receive priority attention.
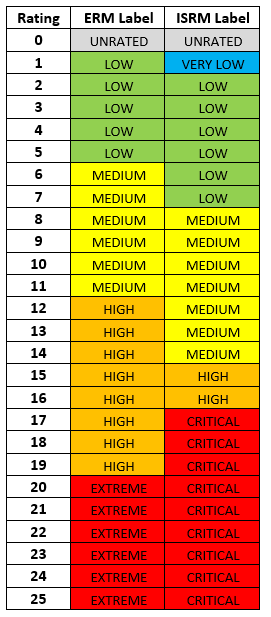
To summarize, the risk rating scale used for Information Security Risk Management (ISRM) within the Government of British Columbia is as follows:
| ISRM Start Rating | ISRM End Rating | ISRM Risk Rating Label |
|---|---|---|
| 0 | 0 | UNRATED |
| 1 | 1 | VERY LOW |
| 2 | 7 | LOW |
| 8 | 14 | MEDIUM |
| 15 | 16 | HIGH |
| 17 | 25 | CRITICAL |
If you deal with Enterprise Risk Management (ERM) within the Government of British Columbia, you will notice that the above rating scale differs from the ERM rating scale below:
| ERM Start Rating | ERM End Rating | ERM Risk Rating Label |
|---|---|---|
| 0 | 0 | UNRATED |
| 1 | 5 | LOW |
| 6 | 11 | MEDIUM |
| 12 | 19 | HIGH |
| 20 | 25 | EXTREME |
To reconcile risk ratings between ISRM and ERM where the need arises, the following translation table can be used.
Risk rating diagram:
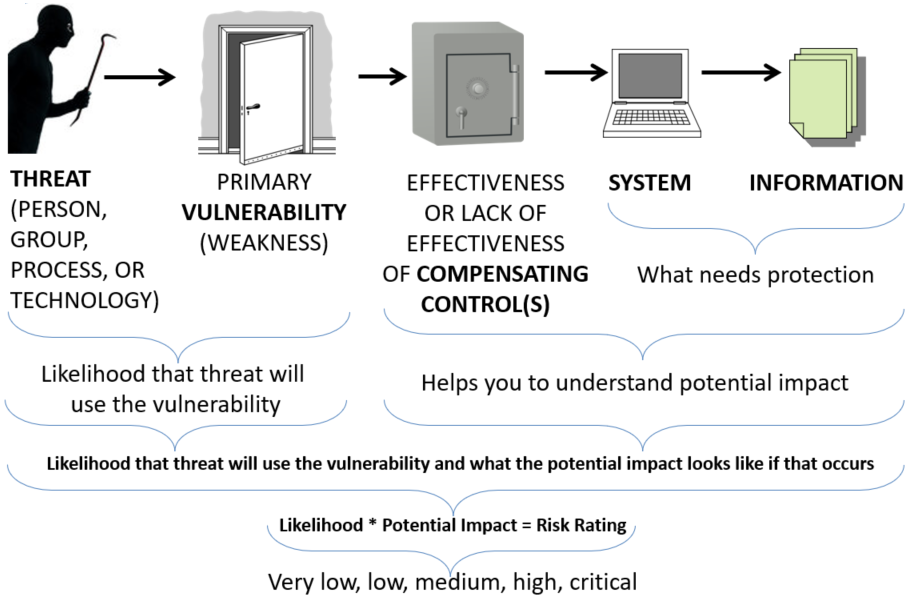
How can one understand “likelihood”?
Consideration should be given to the occurrence of already substantiated incidents and known exposures. This is explained as follows:
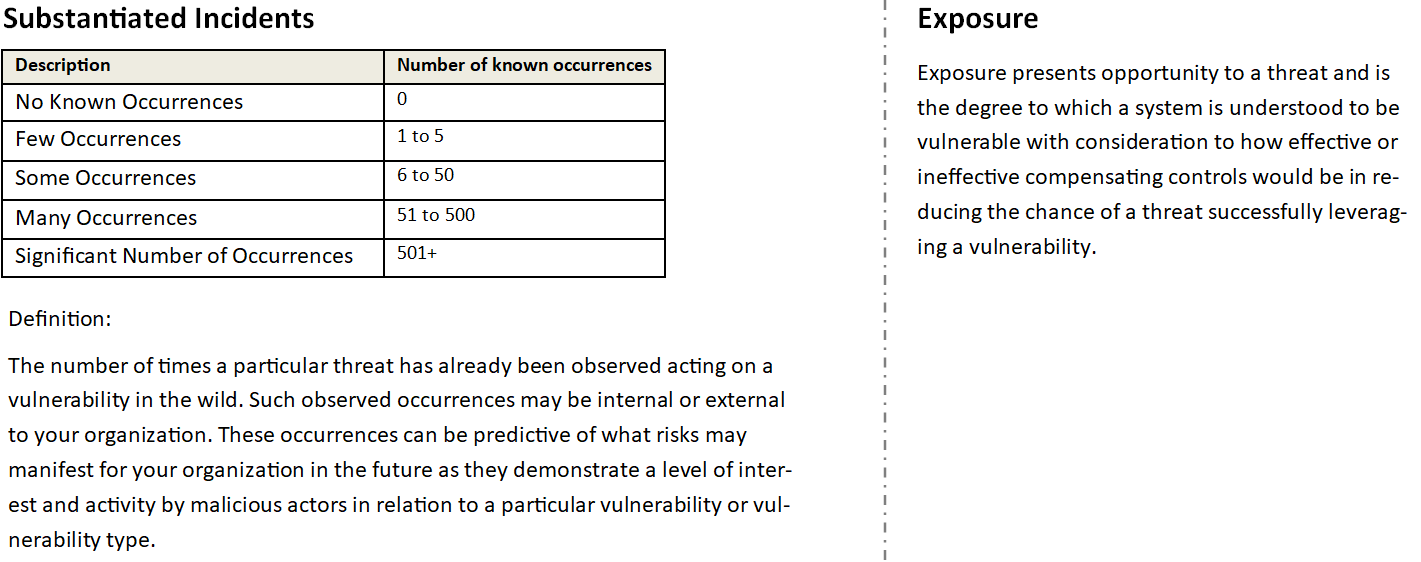
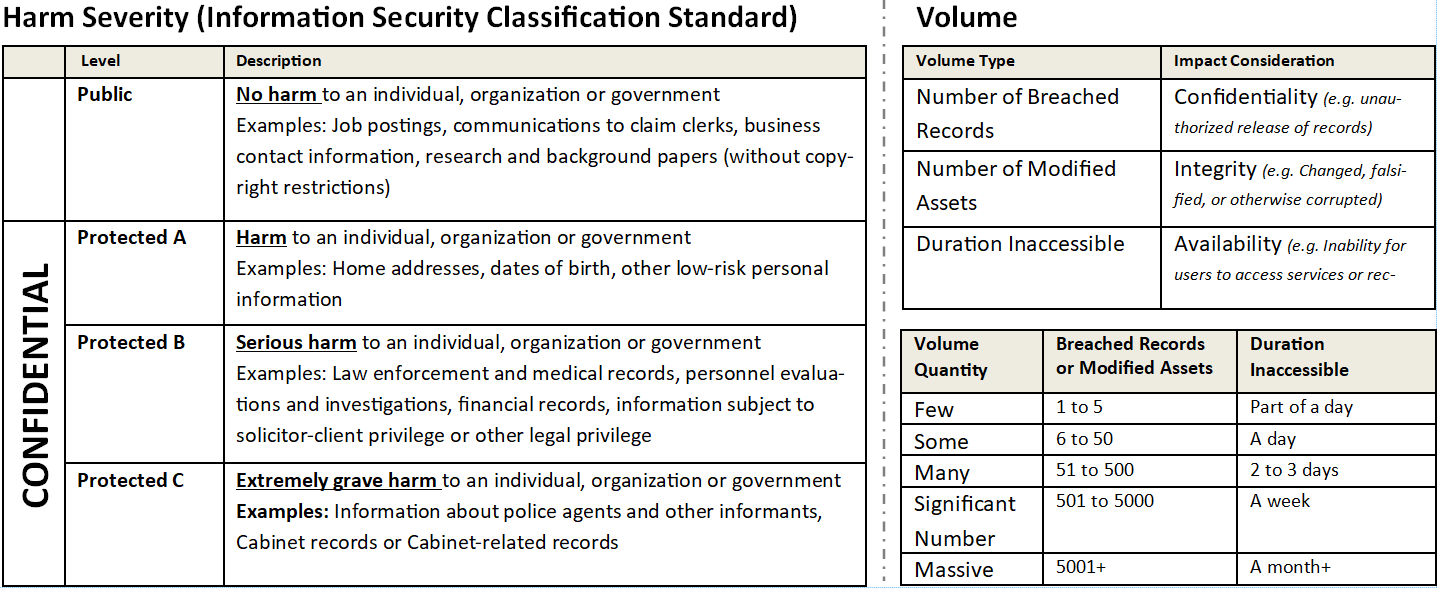
How can one understand potential “impact”?
Consideration should be given to the harm severity and volume. This is explained as follows:
What is the different between a Security Threat Risk Assessment (STRA) and a risk register?
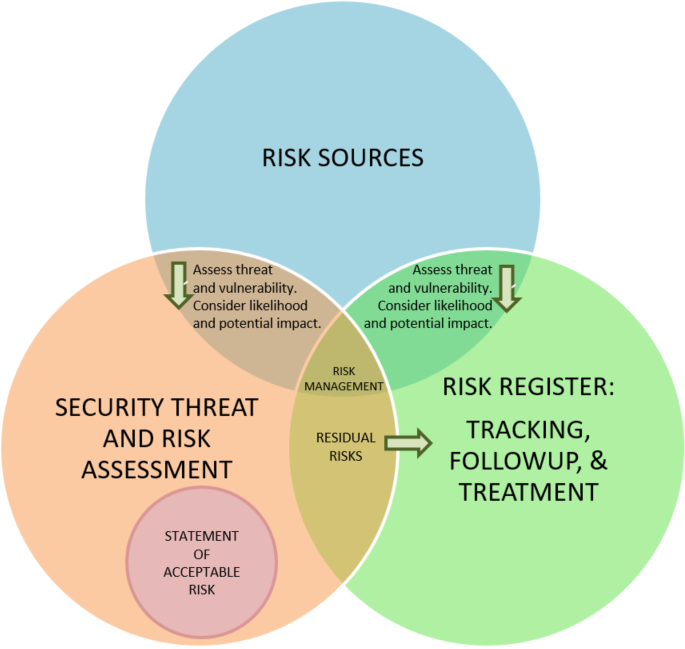
Common “threats” to consider
- Nation State sponsored groups
- Organized crime groups
- Amateur criminals
- Hacktivists
- Terrorists
- Disgruntled insiders
- User or administrator error
Common “vulnerabilities” to consider
- Weak Encryption
- Buffer Overflows
- Unvalidated Input
- SQL Injections
- Cross Site Scripting (XSS)
- Broken Authentication
- Session Management
- Insecure direct object references
- Security misconfiguration
- Cross-site request forgery
- Race Conditions
- Insecure File Operations
- Humans (e.g. Social Engineering)
