Risk Appetite and Register
Defining the organization’s risk appetite is crucial; it assists in determining if implementing new technologies is within an organization’s risk tolerance. Also, an organization’s risk appetite informs the risk register, in which the residual risk should fall within the risk appetite for each activity/item listed on the register.
The register should typically have the name of the risk item or activity, the risk involved in using that item (this is the inherent risk), the controls in place to mitigate the risk, and the risk left after the control(s) have been applied (known as the residual risk). Identifying the organization’s technology adoption level can assist in defining the risk appetite.
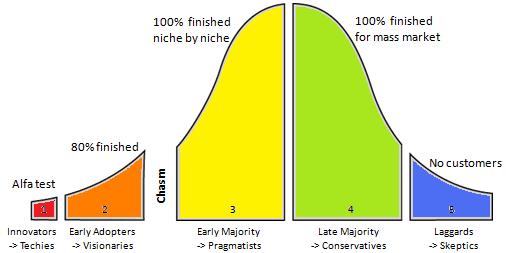
Based on the technology adoption lifecycle, Laggards are placed at a low risk level, Late Majority are placed at the mid-low risk level, Early Majority are placed at the mid-high risk level, and Early Adopters and Innovators are at the high risk level. (See table below). The ideal risk level for government organizations depends on the nature of their business and is usually between Early Majority and Late Majority.
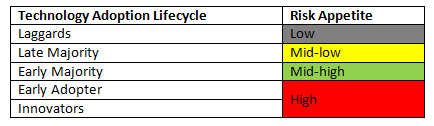
Take “A” as an activity/item on the risk register, “IR” as the inherent risk, “C” as the control(s) in place, “RR” as the residual risk, and “RA” as the risk appetite, the risk register should follow this mathematical principle:
A(IR) + C = RR <= RA; meaning that the Residual Risk should be less than or equal to the defined risk appetite.
Control Objective
There should be a risk register in place which identifies the risk appetite, and the list of risk items/activities in the business operation. The risk register should also include inherent risk, the controls in place, and the residual risk.
